Intro
I saw this paper the other day. Was searching for other things, but the title intrigued me
People call blockchains decentralized. Yet they store the private key in a single place. The phrase “Not your keys, not your coins” is ancient wisdom. Still it ignores a fundamental issue: a single point of failure.
Given today’s threat landscape, decentralizing keys is just as important as decentralizing consensus. Techniques like secret sharing and threshold signatures help. But they were already mainstream between 2018 and 2021.
The problem? Even with these schemes, usability constraints force people to store key shares on just two or three servers. Often secured by the same password. An attacker with a few extra hours can still drain six or seven figures. It’s barely an improvement.
I found this paper fascinating. Hope you’ll appreciate the novelty too.
The Problem with Today’s Systems
Many cryptocurrency systems depend on private keys. These keys serve as digital access points for your funds. In many setups, users send their keys to a server for storage. This method creates many risk. From the inside, server managers can censor you, steal your keys and funds. From the outside, if attackers breaches the server, they may gain access to your private keys. It is like giving someone a spare key to your house and hoping they keep it safe and will not use to steal inside. Not your keys, not your coins.
Sometimes outsourcing storage is inevitable. Think hardware wallets. Even if you store it in a Ledger, it still behaves as cloud services, even if offline. In those cases, you encrypt the key with a password, so the server doesn't know what's stored in there. You solve 99%+ of the inside threats.
Still, this design doesn't prevent offline attacks. Meaning: it lets an attacker try many password guesses if they steal data. Like guessing the code to a lock until succeed. When the attacker finds the correct password, he gains full access to the funds.
The risk of a single breach means that one mistake can lead to a complete loss of funds.
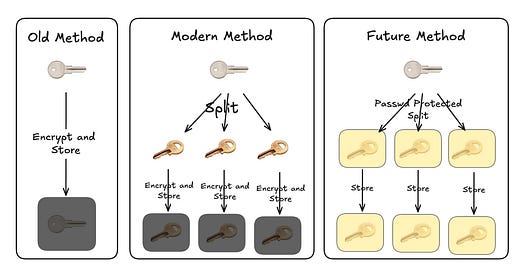
The Solution: Augmented Password-Protected Threshold Signatures (aptSIG)
This method splits your key into parts and spreads them across several servers. It does that using secret sharing. In short: Imagine a safe with several locks. You need enough keys from different locks to open the safe. Even if someone gains access to one or more of these servers, they still cannot build the complete key.
Secret sharing the key does not prevent the servers (plural) to know they have a key though.
aptSIG changes this picture completely. It splits the key into password-protected pieces. Even if an attacker breaches every server, they face a big hurdle: the password. Even if the attackers steal the pieces, they also need a password to combine the pieces. In other words, the attacker cannot gather all the parts and then work on one password-protected file. They must still guess the password to reassemble the key.
This makes offline dictionary attacks 99.9% impossible. Why? Because with no password the attacker cannot even build the file to work on in the first place! They must have the correct password to stitch the pieces together.
In essence, aptSIG builds a safety net with two strong layers. One layer spreads the key out so that no single breach gives away too much. And you can also encrypt these pieces. The other layer uses a password that the attacker must overcome, even if they have all the parts.
TL;DR: This approach makes your funds safer. It splits the secret key into parts and adds a final check with the password. This extra step stops bad actors from easily breaking in, protecting your assets in a way that simple encryption cannot.
Practical Applications and Use Cases
New protocols are as cool as the ability to use them, both for developers and users. This one is usable.
Integration into Existing Systems
Developers can add this method into current digital wallet systems. The system works well with common threshold signature schemes such as those for ECDSA and BLS. So it supports Bitcoin and Ethereum at least.
Enhanced User Experience
This is a big one: Users continue to use a familiar password-based interface. The system adds extra safety on the back end by spreading the key into pieces. This way, users do not need to learn a new way to protect their funds. At the same time, their assets receive stronger protection.
Beyond Cryptocurrency
This idea goes further than digital wallets. You can use this method to secure any distributed task that uses a key. For instance, any multi-party computation that relies on a key can benefit from this approach. This opens the door to many different uses in various areas of technology.
Challenges and Open Problems
Some users believe that their current systems are safe, even when they are not. This belief makes them less willing to try new methods that actually offer better security. Also. Developers often stick with the familiar tools. Not all devs are confortable in cryptography and learning a new methods takes time and effort.
To be fair, splitting the key into parts can slow things down or create issues if one of the servers is not available. It's why companies mis-implement threshold cryptography in the first place. There is a need to balance stronger security with keeping things fast and simple. People in the crypto community must be willing to test and give feedback to see how this method works.
Nothing new under the sun, these are structural problems that hinder progress generally.
Blockchain may be considered decentralized, but your keys are not. How long will you wait before your weakest link becomes your biggest regret?